Frequently Asked Questions
General Questions
This collaborative, national program is designed to strengthen cybersecurity at Canada’s research and education organizations by aligning, coordinating, and funding cybersecurity initiatives that can deliver the most impact to participants.
The federal government department Innovation, Science and Economic Development Canada (ISED) is funding CANARIE to coordinate, align, and invest in the initiatives of the program.
Participation is open to Eligible Organizations (see criteria below). Participation is limited to one application per organization.
To be eligible to participate in this program, an organization must be:
- A post-secondary institution, a non-federal research facility, or a Centre of Excellence;
- Connected to Canada’s National Research and Education Network (NREN) and a member of a provincial or territorial NREN Partner; and
- Connected to that NREN Partner through an autonomous network.
There is no deadline for participating. Once enrolled in CIP, your organization will be able to sign up for funded services. Note that each CIP service has its own sign-up process. Enrolling in the program does not automatically enroll your organization into every service.
It depends on the initiative. For cyclical services such as the National Cybersecurity Assessment and Benchmarking Service, yes. Contact [email protected] to learn about the timing of the next cycle of these services. There is no deadline for signing up for the Cyber Threat Intelligence service.
There is no such obligation, but CIP-funded initiatives are intended to integrate with each other to strengthen cybersecurity at the organization level, and in turn the overall security of the entire sector.
CIP does not provide direct funding to organizations; rather it funds initiatives that are delivered at no cost to eligible organizations.
Funded initiatives are available to eligible organizations that are participating in the Cybersecurity Initiatives Program. If your organization is eligible to participate in the CIP, the NREN Partner in your province or territory will contact you with a link to the program’s participation form. If you have questions about your organization’s eligibility, please contact [email protected].
The form asks you for information that will help populate standard fields in the Organization Cybersecurity Collaboration Agreement (OCCA) with CANARIE. You can preview a sample participation form and OCCA.
The OCCA is an agreement between CANARIE and an Eligible Organization (EO) that has decided to participate in the Cybersecurity Initiatives Program. The Purpose of the OCCA is to formalize the Eligible Organization’s intent to collaborate and participate in national cybersecurity projects and initiatives, and benefit from CANARIE’s funding of those initiatives.
Preview a sample OCCA.
For consistency across the sector, all participants in the Cybersecurity Initiatives Program are required to execute the same agreement. The OCCA cannot be modified for individual participants.
Cyber Threat Intelligence Service
The source of threat intelligence is the same, but the level of protection offered by each is very different. The integrated CanSSOC Threat Feed is one of the intelligence sources that the CIRA DNS Firewall uses to determine which malicious DNS entries / sites to block from user access.
The direct CanSSOC Threat Feed service is ingested by your next-generation firewall to block external threats from entering your network. It provides threat protection from external sources trying to gain access to your network.
CanSSOC Threat Feed also includes monitoring and reporting services to help identify and mitigate potential threats originating from the dark web.
This initiative is not intended to replace threat feeds you may already have in place but to strengthen them with sector-specific intelligence. The CanSSOC Threat Feed may also contain other feeds that you subscribe to, such as the feed from the Canadian Centre for Cyber Security.
The CanSSOC Threat Feed consolidates and curates several feeds, uniquely focused on risks for the research and education (R&E) sector. Due to the sophistication of today’s cybersecurity threats, a risk at one R&E organization can easily create a ripple effect for the entire sector.
The Threat Feed enables Canada’s R&E sector to draw upon a collective nationally based defense to support organizations.
The technical onboarding session takes about two hours, fully guided by a member of CANARIE’s Threat Intelligence team.
The Threat Feed was developed with the intent that after a small amount of basic configuration, your organization can “set it and forget it” by using it in your end point detection devices.
The only expertise required is a firewall administrator with the skills and permission to access and make changes to your organization’s firewall.
No, but to maximize the Threat Feed’s value, a next-generation firewall is recommended.
The CanSSOC Threat Feed readily integrates with the Cisco Firepower, Fortinet FortiGate, and Palo Alto Next Generation Firewall, but integrations with other next generation firewalls, and endpoint detection and protection devices are under development.
Cybersecurity Benchmarking Service
The Benchmarking Service provides an evidence-based security posture assessment that includes comparisons to other research and education organizations’ performance and to best practices. It is based both on surveys and findings from external monitoring services. It also tracks progress of the overall research and education sector against a set of best practices. Benchmarking data and reports are frequently used by organizations to plan security improvements and to promote the importance of investments in cybersecurity throughout their organization.
Continuous Monitoring provides a feed of nightly security observations which provide an external view of important facets of each organization’s ongoing risks. This is particularly useful for organizations that do not have mature vulnerability management practices in place to protect their servers and other critical resources. It also provides information that research and education organizations often lack, such as detection of compromised end-user devices, vulnerabilities in remotely hosted systems, and many misconfigurations. Continuous Monitoring can reveal infected devices gone undetected, missed vulnerabilities, misconfigurations in email, web applications, and more. This type of detailed information is difficult to acquire for many organizations and beyond the resources of others.
BitSight can provide cybersecurity reports on over 200,000 organizations. The reports contain cybersecurity rating information and the organization’s scores against 23 risk vectors. The reports are available on request in one of two ways:
- Weekly reports for vendors used by your organization. For example, you may wish to monitor your LMS vendor’s security performance for a year.
- Ad hoc reports for vendors you are considering purchasing online services from. These are one-time reports as needed.
Unlike security-maturity assessments that are largely survey-based, Cybersecurity Benchmarking Service combines forensic data from external monitoring services (e.g., BitSight) with complementary participant surveys. This approach aids in contextualizing data, supports the generation of detailed results, and helps inform your organization’s security planning and ongoing improvements. It also helps identify the methods and best practices that made a difference at other organizations.
The working group is made up of organizational representatives who receive access to the BitSight portal, receive comparative reports, complete surveys, and receive survey results. The working group also discusses results, especially in relation to security practices, and influences the evolution of the Cybersecurity Benchmarking process. The working group uses a mailing list, document sharing site, surveys, and workshops to collaborate. Working group members have access to every organization’s Benchmarking scores and ratings but not to their detailed findings or forensic data and not to their survey responses. Working group representatives are bound by the terms and conditions of their participation to keep all organizations’ ratings and scores confidential.
BitSight is a cybersecurity rating service that provides cybersecurity ratings and scores for over 200,000 organizations. Rating and scores are available for purchase by anyone. Much of the data used in this initiative is purchased by CUCCIO from BitSight. CUCCIO cannot control who else may decide to purchase ratings and scores directly from BitSight.
However, only members of the Benchmarking working group are provided access to your scores/data and they are bound to keep them confidential. Your scores will appear more broadly in some reports without being attributed to your organization. For example, working group representatives may share the final year report with their CIOs but the report will not identify specific organizations.
Presentations about the project provide broader and less detailed information on the progress of the research and education sector, again without identifying the performance of specific organizations.
CanSSOC analysts will have access to the security observations (data) that you receive each night as part of the Continuous Monitoring component of this initiative. CanSSOC analysts use the data to alert organizations about risks and threats that may impact them.
Much of the data will be provided via a survey, with topics including:
- Complexity index, which is derived from the number of full-time-equivalent employees and students, as well as research revenue
- Network breakout definitions based on the public IP address space of your wireless and other networks, primarily populated by user-owned devices and the rest of your campus network
- Email security
- Detecting and responding to compromised systems
- Preventing infections on wireless networks
- Multi Factor Authentication
- Security posture (larger survey based on data from Jisc, the IT infrastructure and services provider for the UK’s research and education sector)
- Vulnerability management
- Remote work security
Security teams can measure their progress on best practices and risk vectors while also comparing their performance to their peers.
CIOs can use Benchmarking data to report to their executive, audit committees, and boards to help evolve their organization’s cybersecurity practices and investments.
Benchmarking has already been successful in identifying a set of data-driven best practices and in helping individual organizations compare their performance in these and other areas. For example, in 2018, the Benchmarking team discovered a correlation between improved compromised device scores and the use of next generation firewalls in combination with DNS firewalls. This became a recommended practice that has been tracked every year. Similarly, the team has been tracking progress and promoting the use of multifactor authentication since 2018. CISOs and security leads at organizations frequently report that their participation has helped drive security investments and improved practices within their organizations.
You may already be measuring key metrics of your cybersecurity practices for items such as efficacy and performance. You may also be participating in cybersecurity assessments that analyze your organization’s cybersecurity controls and the ability of the controls to remediate vulnerabilities. These are typically performed against a framework such as NIST, or a cybersecurity standard checklist.
In comparison, benchmarking is the process of comparing to a standard set by peers and links to both measurement and assessment, and to comparisons over time. For more information about the distinction between these three practices, read this blog post.
CUCCIO Benchmarking complements traditional survey-based assessments and full maturity assessments based on cybersecurity frameworks. It is not designed to replace them.
Benchmarking presents an opportunity to evaluate performance in critical areas based on evidence of risk vectors such as compromised devices, out-of-date server and desktop software, email system configurations, and more. The data is collected from over 120 proprietary and open data sources. Benchmarking also allows you to compare your performance and best practices against your peers in detail and in ways not normally available through traditional security maturity assessments.
CANARIE’s CanSSOC Threat Intelligence team will have access to the same security observations (data) that you receive each night as part of the Continuous Monitoring feature. They use the data to alert organizations about potential risks and threats.
Working group members have access to all organizations’ Benchmarking scores and ratings but not to their detailed findings or forensic data and not to their survey responses. Working group representatives are bound by the terms and conditions of their participation to keep organizations’ ratings and scores confidential.
Cybersecurity Benchmarking Service provides ways to compare your progress to other research and education organizations and to the practices that have resulted in better performance by organizations of similar size and complexity to yours. Information is gathered via surveys that are not available from similar services. For example, this Cybersecurity Benchmarking Service tracks adoption of multi-factor authentication, how firewalls are used to protect assets, vulnerability management practices, and more.
The approximate cost of purchasing licenses for Benchmarking, Continuous Monitoring, and Vendor Assessments is $4,800 annually. The cost is covered for eligible organizations that have enrolled in the CANARIE Cybersecurity Initiatives Program (CIP).
There are two onboarding forms to complete and six short surveys. They are spaced out so that each survey is available for two weeks, often with a week or two in between. The working group provides input into what should be asked and how the surveys are structured. We anticipate the surveys will evolve as we work with the soon-to-be launched NREN Cybersecurity Assessment initiative to avoid duplication and to ensure the Benchmarking and NREN Assessment processes complement each other.
There are no technical implementations or maintenance requirements to participate in Cybersecurity Benchmarking. Research & education (R&E) organizations of all sizes and capacities are encouraged to enroll. The more organizations that participate, the more robust the dataset and the greater the benefit to the entire R&E sector.
Support is provided by contacting the Cybersecurity Benchmarking Service team directly and by sharing information within the working group of participants.
There are several companies that provide a similar service. After a brief evaluation, CUCCIO selected BitSight in 2017. It is a comprehensive, one-stop shop that collects data from 100+ sources and collaborates with several data partners (many exclusively) who specialize in various types of telemetry.
CUCCIO is currently testing other data services as part of Continuous Monitoring and will consider using them for Benchmarking.
BitSight provides three types of data:
- Overall rating
- Letter grades (as well as scores out of 100) for things like botnet infections, potentially exploited systems, spam propagation, SSL configuration, patching cadence, open ports, server software, desktop software, and so on.
- Forensics data – detailed data that determine each grade. Forensics data is normally only available to the company or organization being rated. For Benchmarking, each organization provides permission for CUCCIO to download forensic data for analysis.
Summary PDF reports and CSVs are available via the BitSight portal, which reveal your organization’s alignment with the NIST Cybersecurity Framework or with ISO 27001 that include BitSight grades.
National Cybersecurity Assessment (NCA)
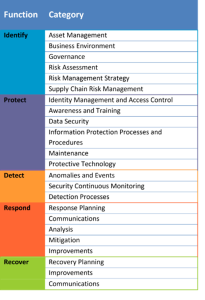
A cybersecurity self-assessment is a way of evaluating security controls to determine your organization’s overall security posture. The National Cybersecurity Assessment uses the US National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), which is broken into 5 functions and 23 categories. The assessment asks a series of questions to determine how well your organization is doing in each category and helps identify the areas that pose the greatest risk.
The perspectives that a cybersecurity self-assessment will offer you differ from what an external cybersecurity audit or assessment reveal. An external audit is a point-in-time evaluation that verifies that specific security controls are in place. However, a cybersecurity assessment is a high-level analysis that determines the effectiveness of those cybersecurity controls to rate your organization’s overall cybersecurity maturity against an established framework (in this case, the NIST CSF).
The final report that your organization will receive will help answer a number of questions, including:
- What are our organization’s current cybersecurity strengths, gaps, and risks?
- What is the current maturity of our organization’s cybersecurity program?
- How does our organization measure up against an established cybersecurity framework?
- Where should our organization focus our cybersecurity spend?
- How does our organization’s cybersecurity capacity compare to similar organizations?
The NCA self-assessment uses a curated set of control questions based on the NIST Cybersecurity Framework, with a set of multiple-choice answers that follow the Capability Maturity Model Integration (CMMI) progression. By participating in the assessment, your organization gains insights into the extent to which your organization is actively and effectively addressing cybersecurity across the comprehensive range of CSF functions and is provided visual representations illustrating areas to address to enhance overall cybersecurity posture. A self-assessment using the NIST framework delves into three significant areas:
- the extent to which risk management processes are formalized and informed by organization-wide business/mission requirements, risk objectives and your threat environment
- The extent to which your organization has an integrated risk management program that supports an organization-wide approach to managing cybersecurity including the communication between senior cybersecurity and non-cybersecurity executives on cybersecurity risk
- The extent of the organization’s external participation with the broader ecosystem to inform its own and the relevant community’s (including supply chain) understanding of cybersecurity risk
Given the breadth of information covered by the questions, the process of responding to the entire set of questions generally involves gathering responses and views from a number of people across an organization rather than having a single person respond to all of the questions.
The CUCCIO Benchmarking service provides a score based on various external scans of your organization. Together, the CUCCIO Benchmarking service and the National Cybersecurity Assessment provide your organization with a comprehensive view of your cybersecurity capabilities and specific areas of strength and weakness.
The NCA and the Benchmarking services are complementary in nature.
Powered by the BitSight platform, CUCCIO Benchmarking scores come from continuous technical monitoring of the externally accessible domains associated with your organization. It can reveal configuration issues, vulnerabilities, and known breach information collected from external sources. BitSight assesses your exposed technology implementation and continuously monitors those technologies for new vulnerabilities.
The NCA service, on the other hand, is a point-in-time self-assessment based on the NIST CSF. This kind of assessment focuses less on technology and more on the maturity of the security processes of your organization. It covers items that are not directly identifiable through a technology-based assessment.
Together, the NCA and BitSight can provide a comprehensive view of your cybersecurity environment, identifying weaknesses that could increase the risk of a security incident if not mitigated. For example, BitSight may provide evidence that your external presence is vulnerable to an attack because it has not been patched. This may lead to the understanding that your patch management and IT security processes are not performing as expected.
Conversely, for example, the NCA may reveal that your business continuity maturity is low, which increases the risk of a longer-than-desired outage in the case of a cybersecurity event.
The National Cybersecurity Assessment identifies gaps and areas of priority for each participating organization. The report provided will include recommended steps your organization can take to immediately improve its security posture, or to better define a long-term cybersecurity roadmap.
The assessment will help you determine your security gaps and overall risk. By participating, your organization will have a better understanding of your areas of strength and weakness, which may help mitigate your risk of a security event.
The Government of Canada, through the Canadian Centre for Cyber Security, made the decision to include the academic sector as one of the sectors of Canada’s Critical Infrastructure to be secured against cybersecurity threats. The NIST Framework is the top cybersecurity framework primarily intended to support the management and mitigation of cybersecurity risk in critical infrastructure organizations.
Even though there are multiple other frameworks in use throughout the post-secondary sector, the NREN selected this central framework for a nationally consistent approach among all participants, and to support funding opportunities in functions (Identify, Protect, Detect, Respond, Recover) where common gaps are identified.
Personally identifiable information (PII) is not required to participate in the NCA. The following data is required:
- Basic contact information (first name, last name, email address) for the individual who will be considered the “questionnaire owner” at your organization. This information is required to set up an account on the Alyne platform, which is used for the NCA questionnaire.
- Data required to calculate your organization’s placement relative to the global complexity index, including student FTE, staff FTE, and research revenue.
- Responses to the multiple-choice questions in the assessment itself.
Organizations will receive three different types of outputs, prepared by the NREN’s National Service Team of cybersecurity analysts:
Report of Assessment Results and Recommendations
Target Audience: Presidents, Boards of Directors, CISOs, Risk Managers, VPs Research, Provosts, Security Teams, CIOs, Vice Presidents of Finance and Administration, Risk and Audit Committees
A high-level summary of the assessment results, including your organization’s maturity level compared to the overall expected maturity level and the five NIST CSF functions, your organization’s top three assessed risks, and recommendations to address those risks.
Comparative Report
Target Audience: Security Teams, CIOs, VPFAs and other executives, Risk and Audit Committees
Visual representations and graphs to allow you to compare your organization to your peers (per the Global Complexity Index).
CIOs can use the two reports above to help prioritize security investments, and to raise awareness of cybersecurity gaps at the executive level and with other stakeholders.
Raw data
Target Audience: Security Teams and CIOs
A PDF and Excel file of the raw assessment data is available in the Alyne platform. Your security team may choose to use this data for its own analysis and to identify strengths and gaps.
Insurance providers use questionnaires to help determine the risk to them in offering cyber insurance to potential customers. They ask targeted questions that do not cover the full spectrum of a security program. This assessment is designed to help participants gain an appreciation for the full spectrum of cybersecurity functions, and their organization’s maturity for each. The intent is that your organization will be able to identify and fill priority gaps prior to being required to by an insurance provider or auditor.
Organizations will save the cost of purchasing a license for a cybersecurity assessment platform, as well as the staff time to extract the data from the tool to determine the risk areas. The service will also offer your organization training, support, and insight over and above what you would receive from simply conducting the assessment on your own.
Having a comprehensive understanding of your cybersecurity posture and taking the steps to mitigate gaps or weaknesses could help mitigate a cyber-attack or data breach. The estimated average cost of each data breach was $7.44 M in Canada in 2021 (Source: Cost of a Data Breach 2022 Report | IBM).
Eligible organizations will be asked to complete a questionnaire once a year within a standardized timeframe.
There are no technical implementations or maintenance requirements to participate in the NCA. Research & education organizations of all sizes and capacities are encouraged to participate. The more eligible organizations that participate, the more robust the dataset that informs regional and national decisions and approaches, which in turn amplifies the benefits delivered to your organization.
Support is provided by contacting the NCA National Service Team directly through [email protected]. A resource library containing self-serve documentation and video tutorials is available at https://nca.nren.ca.
There are 240 control questions encompassing all five functions (identify, protect, detect, respond, recover) of the NIST CSF.
This will vary depending on extent that you need to consult with other groups or colleagues in your organization to provide accurate and informed answers to certain questions. In such cases, you can either choose to engage with those individuals directly (either through consultation or organizing a group meeting) or to distribute responsibility for completing portions of your assessment questionnaire to others, using the delegation function in the Alyne platform.
If a single individual at your organization has all the answers to the 240 self-assessment questions, it would be possible to complete the assessment in less than a day. However, the questionnaire touches on several aspects of your organization, so it is unlikely that a single individual to be able to answer all the questions.
All the reports will be distributed three months after the assessment deadline. However, given the Service Delivery Team will be developing each of the reports individually, the ‘Assessment Results and Recommendations’ report may be delivered to participants earlier if the assessment questionnaire is completed and submitted well in advance of the deadline.
Following a rigorous RFP process to evaluate a platform for this service, Alyne was selected by the NREN Partners as it best met the needs of this national assessment.
To ensure that the aggregate assessments of all participating organizations are included in NCA reports, the questionnaire must be completed by midnight ET on December 15, 2023.
A key value of the National Cybersecurity Assessment (NCA) is that each participating organization will gain insights about how its cybersecurity maturity compares to the cybersecurity maturity of similar organizations. This data will be sufficiently aggregated so as to maintain the confidentiality of each individual organization participating in the assessment.
Data confidentiality will be strictly maintained. All individuals handling your data will be bound by CANARIE’s Confidentiality Agreement. Furthermore, an Appropriate Use Policy will govern data storage, dissemination, and access as well as the use of data to help make data-driven decisions that support the critical needs of Canada’s research and education sector.
Security considerations were prioritized during the national procurement process to acquire a platform to support the NCA service. Alyne’s HECVAT (Higher Education Community Vendor Assessment Toolkit) report was reviewed by the procurement committee, which included CISOs and other security professionals representing Canada’s higher education sector. All NCA data is stored in Canada, proof of data residency has been verified by the NCA Technical Lead, and security ratings of Alyne and of its platform (provided by prominent security risk tools) have been reviewed by CANARIE.
All NCA National Service Team members are bound by both a Confidentiality Agreement and an Appropriate Use Policy that outlines the requirements and limitation of use, dissemination, and storage of NCA data.
The National Cybersecurity Assessment (NCA) offered by Canada’s NREN partners has been specifically designed and developed for Canada’s research and education sector and is available at no cost to all eligible organizations participating in CANARIE’s Cybersecurity Initiative Program (CIP). The NCA will provide a comprehensive view of your organization’s cybersecurity maturity, encompassing all NIST Cybersecurity Framework functions, categories, and subcategories. It does not require you to provide any details regarding your technical infrastructure or breach history.
Beyond an assessment tool, the NCA is a service that is complemented by ongoing training and support offered by cybersecurity analysts on the NREN’s National Service Team. By participating in the NCA, you will receive a personalized report for your organization that not only identifies detailed risks, strengths, and gaps, but also provides guidance on where to make the most critical and impactful investments. In addition, these personalized reports will allow you to compare your organization’s cybersecurity practices and capabilities in relation to comparable organizations, based on the global complexity index (the same classification used in other CIP initiatives, such as the CUCCIO Benchmarking service). The NCA will be conducted on an annual basis, allowing answers from previous assessments to be brought forward and included as comparative data in your future reports.
At the provincial and federal levels, the aggregate information collected through the NCA will build a unified view of the sector to help set priorities for the investment and development of new services.