Table of Contents
- 1. eduroam CAT: Purpose and scope
- 2. Enrolling your organization for eduroam CAT
- 3. Configuring your organization’s properties
- 4. Generating installers for users
- 5. Installer visibility on the user download page
- 6. Verifying your RADIUS setup
- 7. Other features
- 8. Replacing the RADIUS server root CA certificate
- 9. Getting Help with eduroam CAT
eduroam CAT: Purpose and scope
1.1 Introduction
Manual device configuration for Wi-Fi is often error-prone, and critical security settings for WPA2-Enterprise mutual authentication and preferred Enterprise Authentication Protocol (EAP) methods are not available for configuration on devices. This either prevents users from connecting or allows them to connect but with increased risk of attacks such as the harvesting of user credentials.
Devices that are not correctly configured can accept any RADIUS server certificate offered –sometimes without any user intervention. Rogue hotspot operators can then force an EAP downgrade attack to either capture user credentials in plain text, or as hashes which can be quickly broken offline. This can present a significant risk, as these credentials are not typically unique to Wi-Fi access.
eduroam CAT and the accompanying geteduroam app allow the administrator to apply the correct settings to each device to help mitigate these risks.
1.2 What is eduroam CAT?
The eduroam Configuration Assistant Tool (CAT)’s purpose is to allow you, an eduroam Identity Provider (IdP) administrator, to configure profiles and generate customized eduroam installers for various platforms or for the geteduroam app.
These profiles define the settings and acceptable parameters to ensure that user devices are configured to accept only your RADIUS server certificate, and to prevent devices from accepting weaker authentication protocols. The profiles can be customized to include your IdP’s name, location, and logo. You can also include your helpdesk’s contact details and assist users to ensure they use the correct username format. By using CAT, you ensure your end-users will enjoy a great eduroam experience while roaming as well as on-campus. The installers support many languages, so you can offer an installer in your user’s first language!
eduroam CAT also has tools to assist you in debugging your own RADIUS server setup.
eduroam CAT can make the end-user installers available on its own user download area, or you may choose to download them yourself and distribute them on your organization’s own web page. You can also choose to make only a subset of the supported platforms available for direct download, while redirecting users of select platforms to your own support page (e.g., if you have custom installers with non-standard specialties for these platforms).
Many users don’t know which operating system they are using. eduroam CAT works on both PCs and mobile devices and includes operating system detection which automatically suggests how to proceed. It includes an “All platforms” link which takes users to the full platform selection. A screenshot of the download area is below. Try it out yourself: go to https://cat.eduroam.org, and select any organization on the download page!
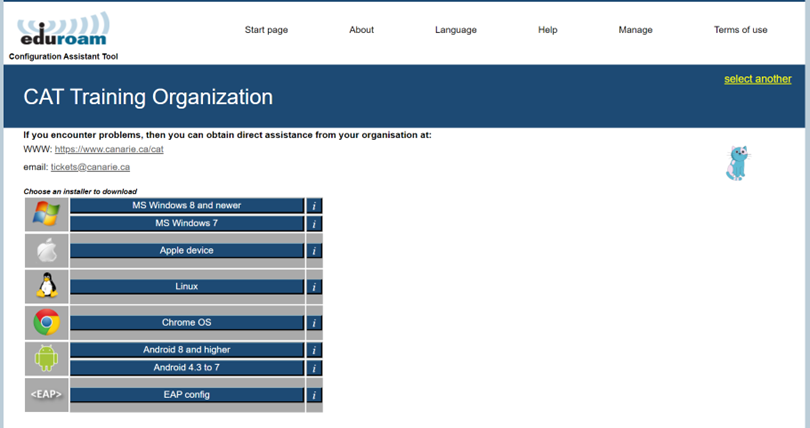
There is also a lightweight download page for resource-constrained mobile devices.
1.3 Device Support
eduroam CAT supports most popular devices and many EAP types. To view the full compatibility matrix of supported EAP types and devices, please visit eduroam CAT, hover over About in the navigation menu and click About eduroam CAT. You will see that not all EAP types are supported on all platforms – we largely rely on the target Operating System’s capabilities.
Some devices either do not support proper automatic configuration or, for various reasons, such support cannot be used by CAT. For select devices in that class, we still offer the possibility for administrators to set a redirect target. Administrators can then create a dedicated support web page to which the user will be sent for local instructions. You can find the list of these devices on the “Installer Fine-Tuning” page (see below). More devices can be added by the eduroam CAT operators. If needed, please contact [email protected].
Note: Android versions prior to 4.3 are not supported. Your helpdesk will have to take care of legacy Android users by other means.
Android 11+ requires the use of the geteduroam app and supporting CAT profile configuration to permit users to get online at all. The CAT portal will redirect users to the Google Play store to download the geteduroam app.
1.3.1 Support Policy for operating systems versions
eduroam CAT typically follows the vendors’ end-of-life dates:
- Microsoft products
- Apple products
- ChromeOS products
- Android products: No clear support strategy. As of March 2023, Android 10 AOSP is the oldest that still receives security updates.
1.4 Scope
eduroam CAT does not replace your helpdesk!
The goal is to provide you with a valuable service by generating secure installers for multiple platforms. The CAT’s installers work on the target platforms, assuming the end-user has not customized and modified their platform to an extreme degree.
With the geteduroam app, we aim to make the installation process and onboarding intuitive and straightforward while supporting as many devices as possible, and ensuring the most secure configurations.
2. Enrolling your organization for eduroam CAT
Step 1: Requestion an entry for your organization
eduroam CAT follows the same organizational model as eduroam: your national federation administrator has control over all the Identity Providers in their country. Note: for Canada, this is CANARIE).
To begin configuring your organizational profiles with eduroam CAT, the primary technical contact at your organization must send an e-mail to [email protected] requesting access to participate.
Once deemed eligible for the service, you will:
- Receive an invitation email with a token included (the token is valid for 24 hours after being sent).
- Copy the token and follow the link in the email.
- Log in to the eduroam Administration interface and start managing your organization.
See the next section for details on organization and profile setup.
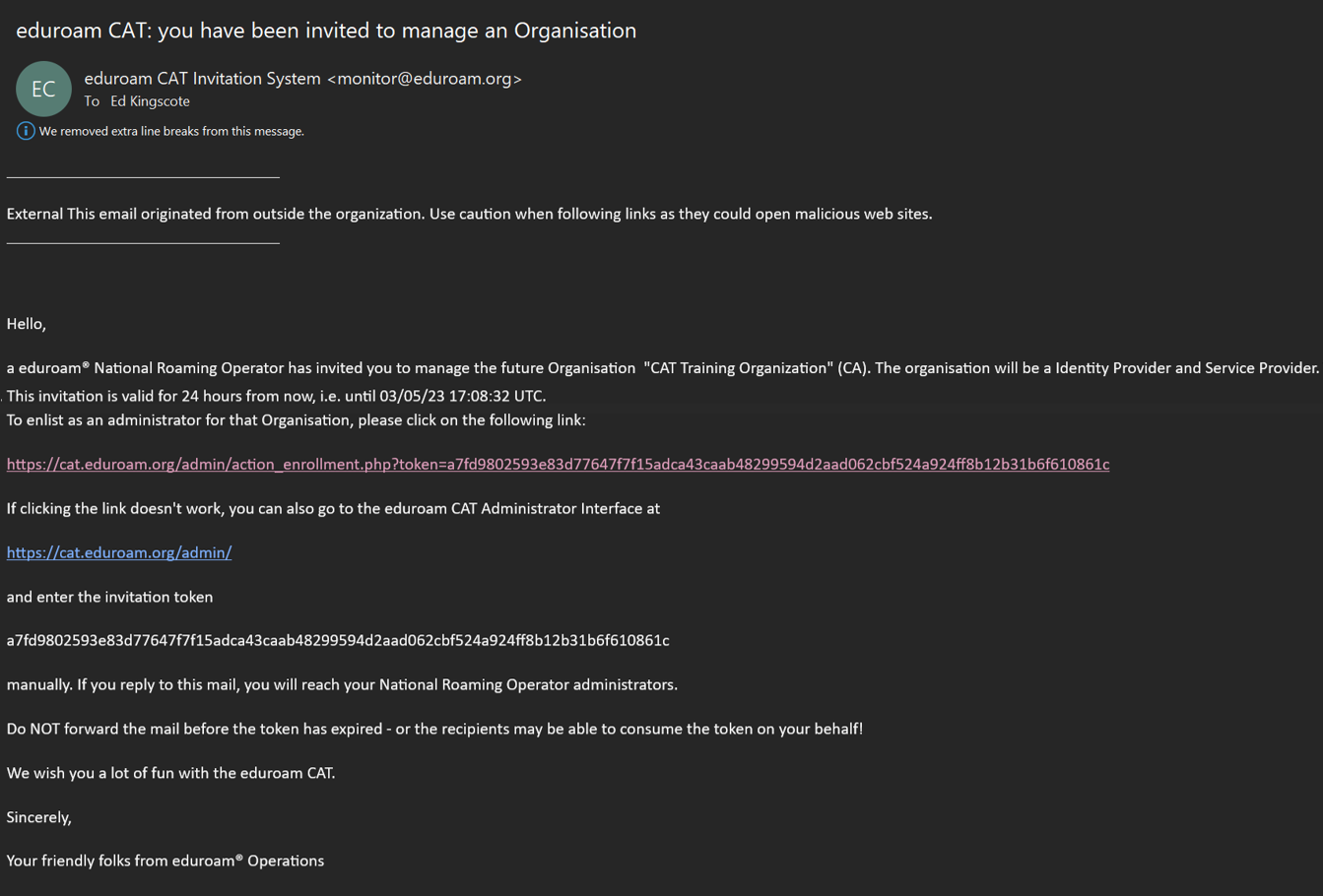
Step 2: Logging in to eduroam CAT
Click the Administration interface link to go to the eduroam Support Services’ federated login service. This login service does not work with site-specific usernames and passwords; instead, you’ll see a list of identity sources.
Choose anyorganization with which you have an account.
Note for members of eduGAIN via the Canadian Access Federation (CAF): If you are a CAF participant with a federated identity management identity provider in eduGAIN, you should be able to click on your organization and authenticate with your home organization’s usual web login credentials. To find out if you are a CAF participant, check here: https://www.canarie.ca/identity/caf/participants/.
Attributes needed in for an R&E federated sign in to eduroam CAT may be one of the following:
- eduPersonTargetedID, Subject-id, Pairwise-id.
- The attributes are checked for presence (and used when a value is found) in this order:
- eduPersonTargetedID,
- pairwise-id,
- subject-id.
For guidance on enabling these attribute(s) to be released or transitioning from one unique identifier to another, please consult your National Roaming Operator and/or IdP software provider.
Notes:
Some organizations may be in the process of joining CAF/eduGAIN but are not production-level members. If this is the case for your organization, you might find your organization’s authentication service in this Experimental list.
If you’re unable log in with your organization’s credentials (e.g., your organization is not an eduGAIN participant), you can also log in using the federated login function of several popular social networks (e.g., Google, Facebook, etc.).
Be aware of your organizational policies regarding using accounts in this context, especially given the role that eduroam CAT plays in helping to secure your Wi-Fi users. You may want to consider creating a Google account solely for this purpose.
Some users may find that none of the options listed suit their organization (e.g., their organization is not an eduGAIN participant and they prefer not to use social networks). We understand that if a user finds the current authentication options unacceptable, they will be unable to sign in. We do not currently have a perfect solution for this issue. As mentioned, you might consider creating a social network account just for the purpose of logging in to the tool.
3. Enrolling your organization’s properties
3.1 Overview
You will need the following information to create an installer:
- General information about your organization (e.g., logo, approximate location, name, etc.)
- Helpdesk contact details (mail, phone, web, etc.)
- Media properties (e.g., SSIDs, wired support, etc.)
- RADIUS and EAP details
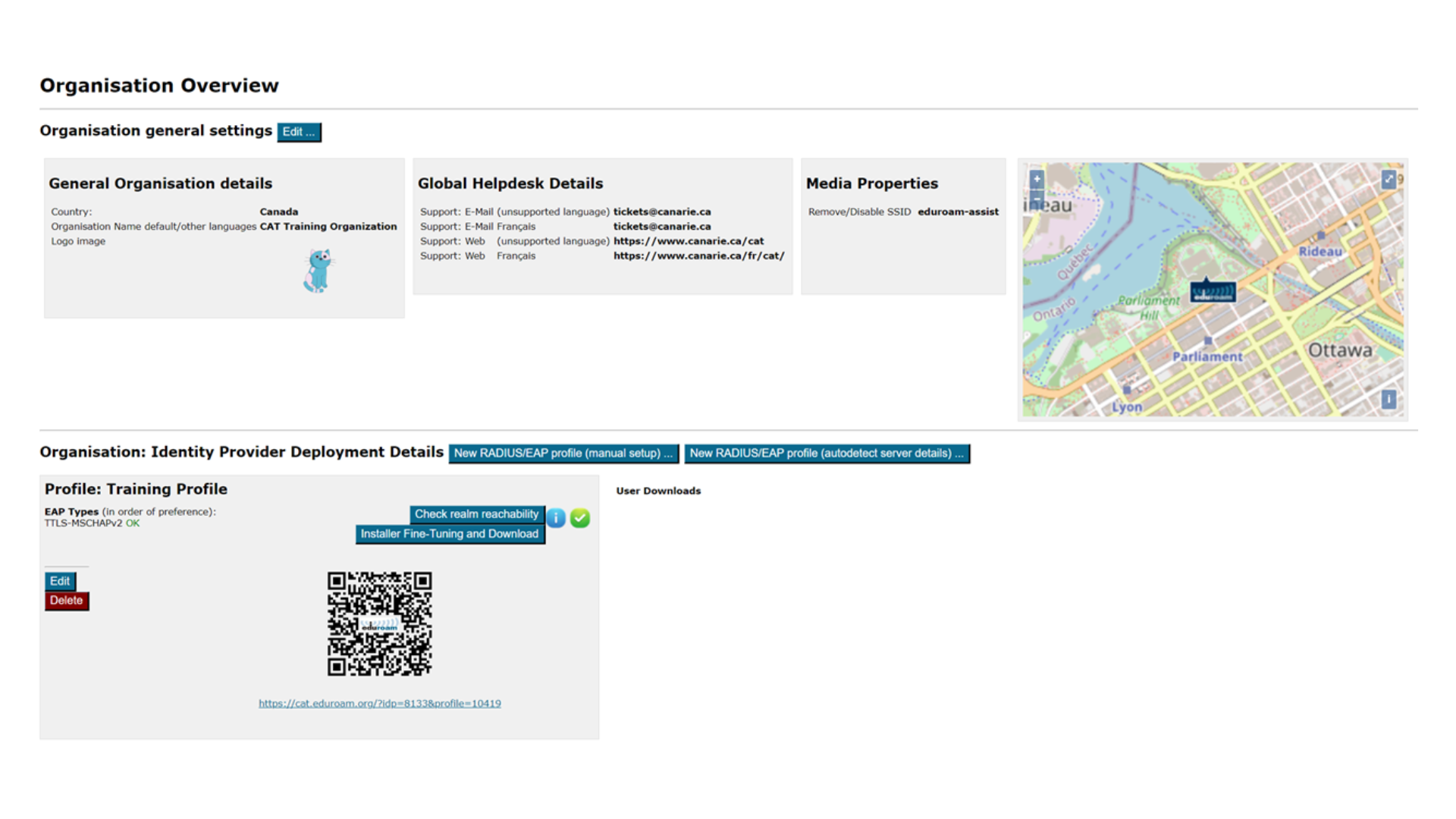
To the largest extent possible, all the information is optional. If you choose not to provide all the requested details, the tool will still create an installer. For best results, please provide as much detail as possible.
There are two governing principles regarding input and storage of information in the administrator user interface:
1. Textual information is offered in several languages; however, values should always be set for the “default/other languages” option. This should align with the primary language used for your communications to your community. You can then choose alternative language(s) to provide multi-lingual options.
2. An organization may use one or more EAP profiles, each having its own EAP-specific settings (e.g., an organization that has both student and staff accounts with different EAP types being supported). Many options in eduroam CAT can either be set for the entire organization or for a specific profile.
Note: If a setting is set on both levels, the more specific profile-level setting will override that which is organization-wide.
3.2 Configuring organizational settings
Once you input the invitation token from your national administrator, you’ll see the “Edit IdP” page. The first time, you’ll be in “wizard mode”, which provides explanatory text regarding the various settings. Each setting has options that you can customize and edit. Don’t be shy – try them all out! Changes will only be saved when you click “Continue” at the bottom of the page.
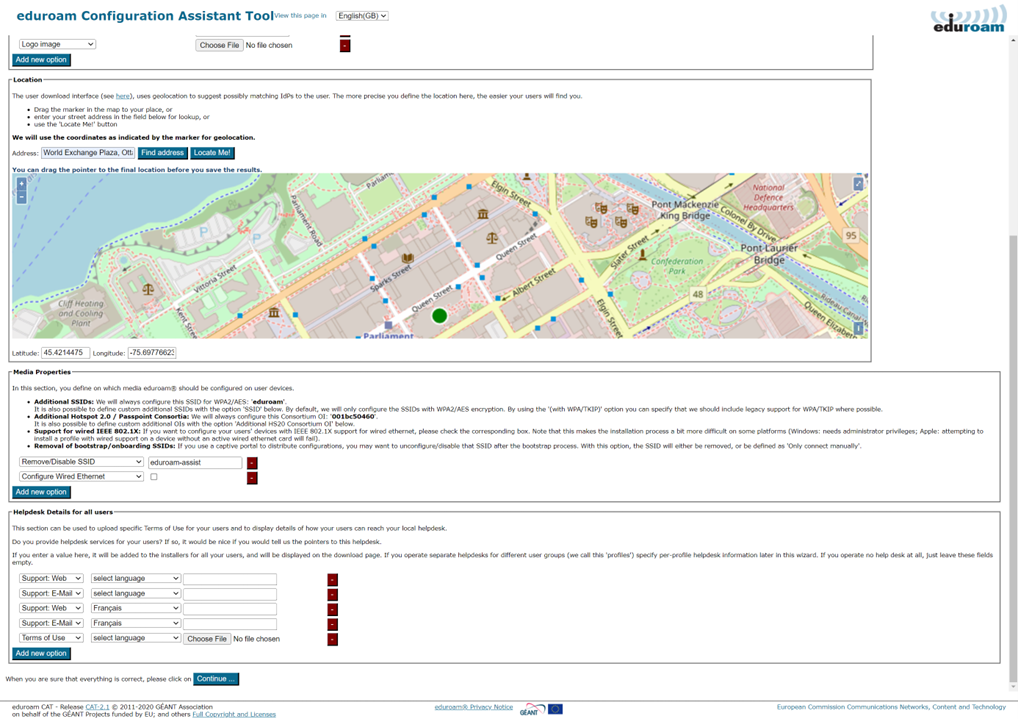
When you re-visit the “Edit IdP” page later from the Organization Overview page, the explanatory texts are condensed so as not to overload the user interface.
You can configure three of the four areas mentioned above on this first page. The RADIUS and EAP settings are configured at a later stage in the Profile configuration section.
3.2.1 General Information
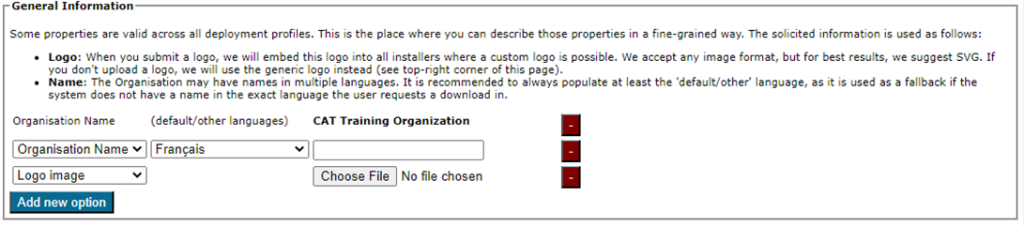
This section sets your institution-wide properties, including uploading your organization’s logo and ensuring your organization’s name is correct.
3.2.2 Helpdesk Contact Details
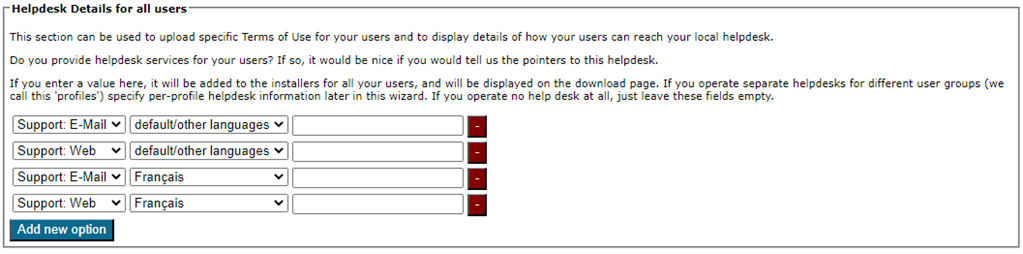
The helpdesk contact details set here will serve as your default helpdesk and apply to any profiles that do not have these details already set.
3.2.3 Media Properties
You can configure all media properties of your eduroam setup in this section.
The SSID “eduroam” for WPA2/AES is always configured as it is the core of the eduroam specification – you do not need to enter it here.
Note: Previous versions of eduroam CAT also installed a WPA/TKIP profile. Since these are now obsolete, current CAT installers will remove this profile during installation.
The list of things you can additionally configure in “Media” are:
Additional SSID for WPA2/AES
If you deploy other SSIDs for which eduroam credentials are valid, you can add these here and they will be configured alongside the eduroam SSID.
This attribute can be set if you want to configure an another SSID in addition to the default SSIDs for eduroam. We strongly recommend only using the default SSIDs. The only exception is if you have premises with a radio signal that overlaps with another eduroam hotspot.
Typical misconceptions about additional SSIDs include the sentiment “I want to have a local SSID for my own users…” In fact, it is preferable to use the default SSID and separate user groups with VLANs. This approach has two advantages:
1. Your users will configure eduroam properly because it is their everyday SSID.
2. If you use a custom name and advertise it as extra secure, your users might at some point roam to another location that happens to have the same SSID name. They might then believe incorrectly that they are connecting to an extra secure network while they are, in fact, not.
Additional own Hotspot 2.0 / Passpoint Consortium OI
If you want to enable Passpoint and have a Consortium Organization Identifier, you can enter it here. The Consortium OI for eduroam is 001BC50460. We do not currently enable this Consortium OI by default. On the end-user device side, settings made for Passpoint will currently only benefit the most recent Apple devices (iOS 7+ and recent-enough hardware, recent Mac OS X).
Whether or not to configure wired ethernet for IEEE 802.1X
Some eduroam participants also use IEEE 802.1X for wired ethernet ports on their premises (e.g., in dormitories). Administrators can specify that the installers should include wired ethernet eduroam configuration on the client devices. This is currently supported for the Windows installers and Apple OS X. Windows installers will provoke a UAC prompt when wired support is turned on.
Note: Wired ethernet is configured in addition to the eduroam wireless service, therefore profiles that are intended for wired use should also meet the same configuration standards as those that are wireless.
Disable captive portal SSIDs after setting up eduroam
Many eduroam participants deploy several SSIDs; typically, a captive portal SSID for help and/or download of configuration profiles/configuration instructions (a “bootstrap” or “onboarding” network), and the real eduroam network. If your users have connected to the bootstrap network before, their devices usually remember it, and may prefer that network over the eduroam network. To prevent this, you can configure the name of your bootstrap SSID, and then during the installation process, CAT will either remove it from the client device, or at least mark it as “do not join automatically”. We recommend the use of an “eduroam-assist” SSID within Canada to support onboarding activities, especially for laptop-type devices that do not typically have cellular connectivity available as a fallback. In this case, you can configure the removal of the eduroam-assist SSID by default here, even if you have not yet established this network in your own organization. This step will save additional work later and better support users who may be doing their configuration at other locations.
3.3 Profiles
Profiles are the specific EAP configurations for your user group(s) and installers are always generated for specific profiles. If you only have one user group, there should be no distinction between organization- and profile-wide settings. However, many IdPs have different user groups which share some properties, but not all. One example is where one profile – the students – have username/password accounts, authenticating with PEAP and generic helpdesk contact points, and another group – permanent staff – have TLS Client certificates with EAP-TLS and have access to a better, second-level helpdesk just for them.
Eduroam CAT makes it easy to manage multiple user group profiles for one organization. Shared properties (e.g., helpdesk contacts) can be defined organization-wide (which makes them immediately available in all profiles), or per-profile (the property then is only defined for this specific profile). You can also define organization-wide settings and override them in specific profiles.
Once you have entered your organization details you will be taken to the organization overview page.
There are two ways of creating a new profile: auto-detection or manual entry of certificate details. We recommend using the automatic method as it can save additional configuration work.

Auto Detection
Auto detection will create a new profile and attempt to pre-populate your RADIUS server certificate details by extracting them. We highly recommend using this as the initial entry point.
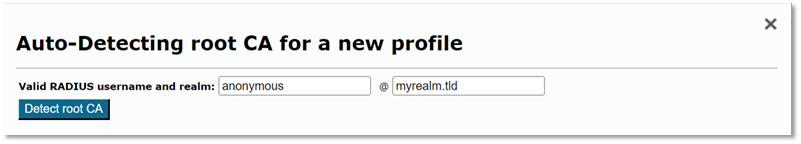
Note: Auto-detection may require a valid username in your RADIUS server; however, some servers are quite happy to provide the necessary information using an [email protected]–style user (adjust to suit your environment).
Auto detection will open the profile page, and you can then validate the settings and continue to make edits.
Manual Configuration/Validation
For a profile, you must first set its name and description. There is also one important option: “Production-Ready.” We will not publish your ge
nerated installers on the end-user download page unless you select this option. This is to prevent accidentally downloading installers with incomplete information while you are still working on the final setup.
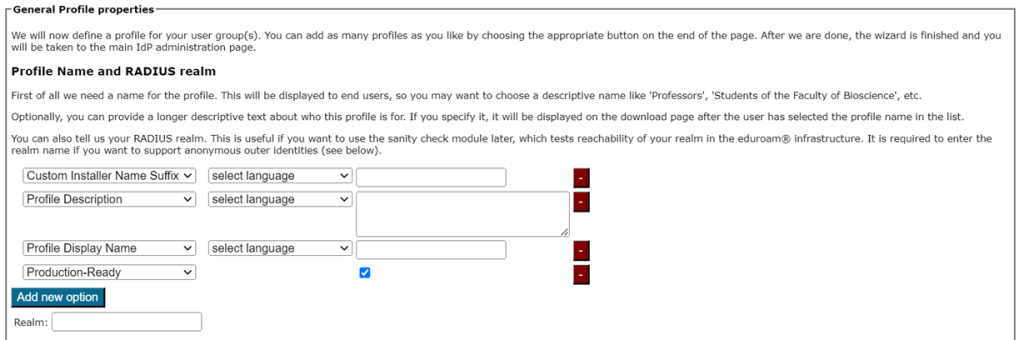
Auto-detection will fill out the RADIUS realm belonging to this profile, but you can still make adjustments, if needed.
Entering the realm is optional, but it is highly recommended as it enables us to do very thorough checks on your RADIUS installation later (see section “Verifying my RADIUS setup” for more details). The realm is also required for anonymous outer identity support on some devices, and you will not be able to enter the CANARIE-supplied anonymous outer identity value later without it.
Note: In Microsoft Windows, the realm for the outer identity is automatically populated from the username from the inner identity.
Additionally, the realm can be used to help ensure correct configuration of the inner identity username (must be either [email protected] or [email protected] depending on the inner identity handling choices).
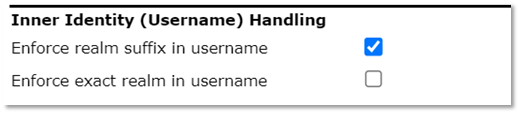
It is highly recommended that you enable the anonymous outer identity to help preserve user privacy.
Canadian organizations must be configured using an anonymous outer identity in the format anonymousXXXXXX, where XXXXXX is the number issued to you by the CANARIE eduroam team. This indicates that you have configured your CAT profile, and signals to both the institution administrators (you) and us (CANARIE) that users are actively using the CAT profile.
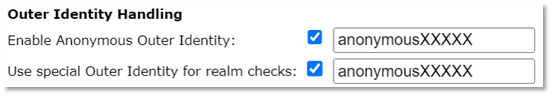
If you don’t want users of that profile to be given an installer, you can also specify that we should send your users to your own support page instead (e.g., if you, the admin, want to generate installers but only download them yourself and present them on your own eduroam support page).
The third aspect of profile generation concerns the EAP types which you’ve configured in your RADIUS server for this user group. If auto-detection has failed, or you need to adjust the values, you can drag and drop all the EAP types you support into the upper green area. The list is displayed in order of preference, so be sure to drag the EAP types into your preferred order (most preferred at the top).
The CAT will always compare the EAP types you’ve configured here with the capabilities of the various devices that are to be configured. If the device supports your preferred EAP type, installers will always be generated for that EAP type. If your preferred EAP type does not work on a given device, it will work through the preference list until a match is found, and then installers for that device will use that EAP type. Finally, if there is a complete mismatch between the EAP types you support and the EAP types on a device, CAT will be unable to generate installers for that device. In that case, we recommend changing your RADIUS setup to support more EAP types.
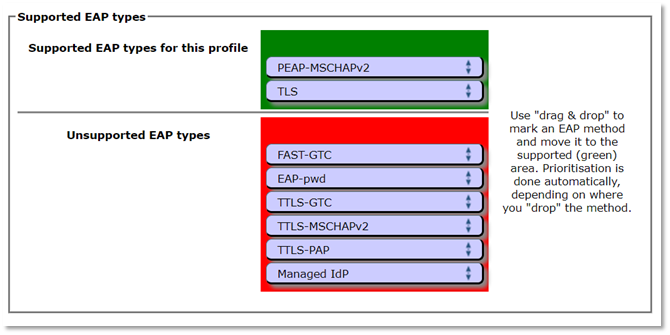
The EAP type configuration is one of the two most critical settings and is a main driver for using the CAT profile. Most devices do not expose this configuration to the end-user, and it’s possible for a rogue access point to negotiate an unsecure EAP authentication method to enable credential harvesting if this isn’t set up.
3.3.1 EAP Details
In the EAP Details section, you can either upload or validate (if auto-detected) the common properties of your RADIUS installation’s EAP configuration.
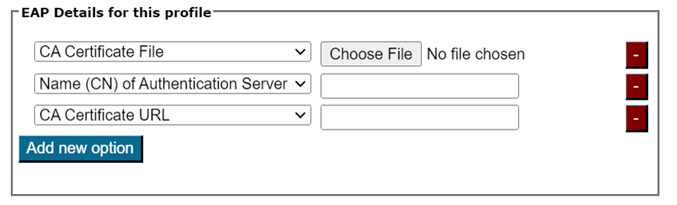
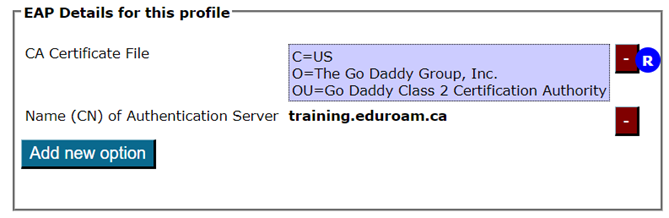
For most EAP methods, the required EAP details are:
- The Certification Authority (CA) certificate(s) which signed your EAP server certificate.
- always include the root CA (indicated by an “R” beside the certificate details after upload)
- optionally, include intermediate CAs (indicated by an “I” beside the certificate after upload)
- The name of your server as specified in the Common Name (CN) of your EAP server certificate.
To avoid problems with some devices, we recommend using a single CN for all your RADIUS servers. See certificate guidance for more details.
Note 1 – Server Certificates
There is no need to upload the server certificate itself. It has relatively short validity and is sent during the EAP exchange during login time to the client. However, the CA certificates ARE required because they are the trust anchor on the client device that is to verify that incoming server certificate, which avoids requiring users to re-apply the CAT profile to their devices each time the certificate is updated.
Note 2 – CA Requirements
Various client device operating systems have specific requirements about which CA certificates and server certificates they accept. For more information, please see EAP Server Certificate considerations.
Note 3 – Rollover Supports
You can upload multiple root CA certificates to CAT simultaneously, which enables CA certificate rollover without a flag day. User devices configured with an upcoming new root CA ahead of time will not notice the change of server certificates from old to new trust root, so long as the Common Name of the server certificate remains unchanged during the rollover.
On the client OS, all root CAs will be installed and marked as trusted. However, the older eduroam CAT Android App for Android (4.3 to 7), will only install one certificate so it can’t be used to support CA rollover. Android 8+ should use the geteduroam App instead, or you can isolate Android users while giving everyone else multiple trust roots first. In this case, you can create a different profile (see next section) just for Android and only load the desired root CA into that profile.
Note 4 – Changing the Root of Trust
Note that any change in the root of trust will require all devices to re-apply their CAT profile using the installers to be able to continue to authenticate securely after the old root of trust is removed.
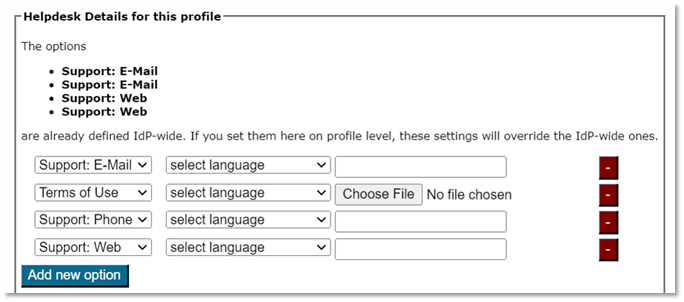
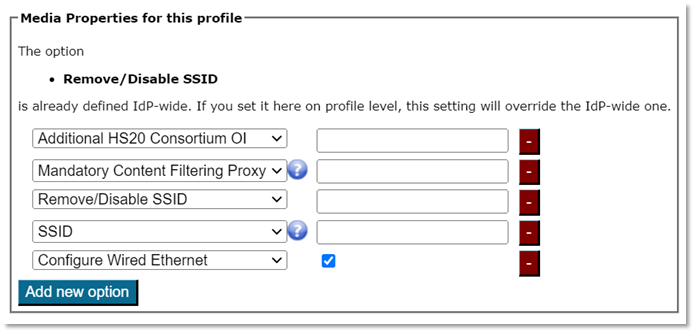
3.3.2 Overriding IdP-wide Settings
After these steps, you can enter/override helpdesk and media properties if you haven’t already done so in the organization-wide settings (see above). If you have entered one specific option organization-wide already, and you enter something different here, the settings on the profile level supersede those on the organization level.
CAT then performs a sanity check of your configuration and will flag any issues. You’ll then be sent to the Organization dashboard. From here, you can continue to download your installers, change organization or profile details, perform sanity checks, and more.
Optional: OpenRoaming support
OpenRoaming is a wi-fi roaming consortium independent from eduroam that uses similar underlying technologies. You can find more details about this consortium and eduroam‘s interaction, and information for eduroam end users at these links.
The CAT tool has specific capabilities to assist end-users for joining OpenRoaming hotspots.
If you are interested in OpenRoaming in Canada, please reach out to us via [email protected].
Full details of the CAT support for OpenRoaming are published on the global eduroam Wiki.
4. Generating installers for users
On the organization dashboard page, you’ll see an overview of your settings.
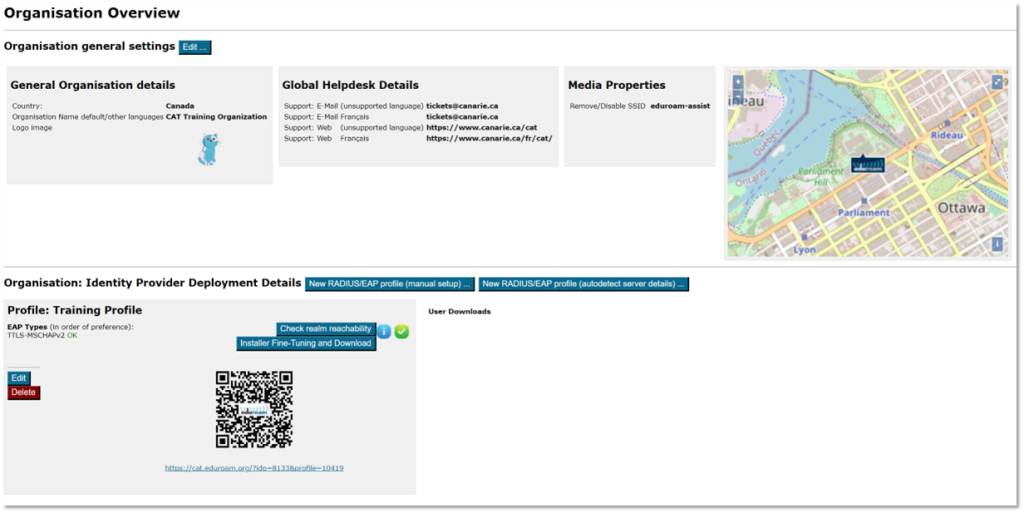
CAT uses this data (and all profile-specific data) to create installers. To get access to the installers, click on Installer Fine-Tuning and Download in your defined profile.
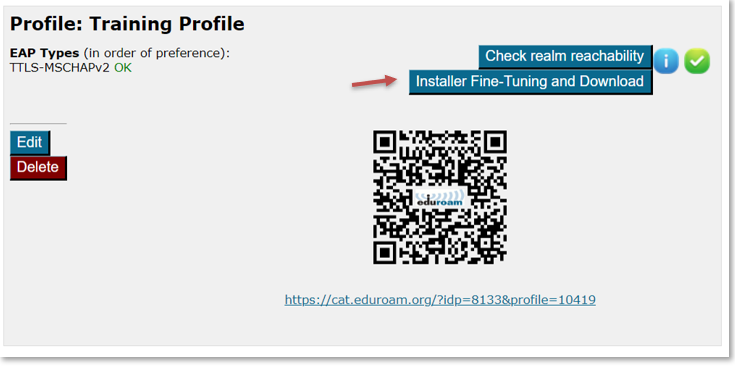
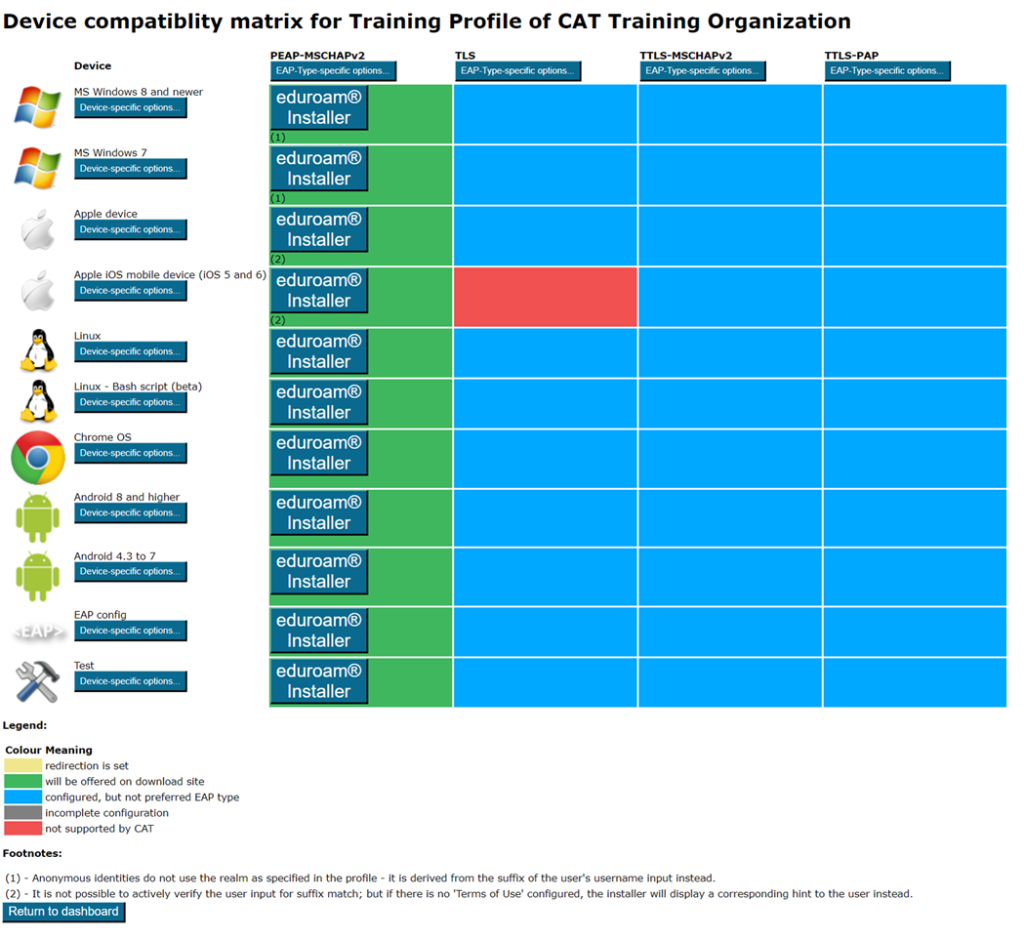
This will take you to an overview of available installers. It is displayed as a matrix of your enabled EAP types – the devices CAT knows about – and whether an installer for all the combinations is available.
 | The installer is ready for use. There is a Download button available. |
 | CAT could create an installer for that combination, but there is a preferred EAP type which it can serve as well which has been generated instead. |
 | CAT does not know how to configure the EAP type on that device. |
 | Required information is missing for CAT to produce an installer. Go back to IdP and/or Profile settings and fill in the missing fields. |
 | You have set up an “exception” and CAT will not offer this combination to end-users, even if an installer may in principle be available (see next paragraph for details). |
Fine-Tuning Scenarios
- You have something special to communicate with your users. For example, hints for which password to use for EAP-TTLS, or which secretariat to turn to to get the client certificate for EAP-TLS?
- You’ve banned Apple Smartphones from your campus and want to alert users to that end?
Solution
For these types of situations, you can:
- Add free text for either specific EAP types or specific devices. This text will be displayed on the user download page before the download begins.
- For devices, you can specify a Redirect target; if this is set, CAT will not provide a download button, but instead will redirect users to the URL you specified. This could, for example, be useful if you have a custom-made or commercial installer for one of the devices, and prefer not to use CATs services for that device. If this option is set, the background for this device will turn white in the matrix (see screenshot above).
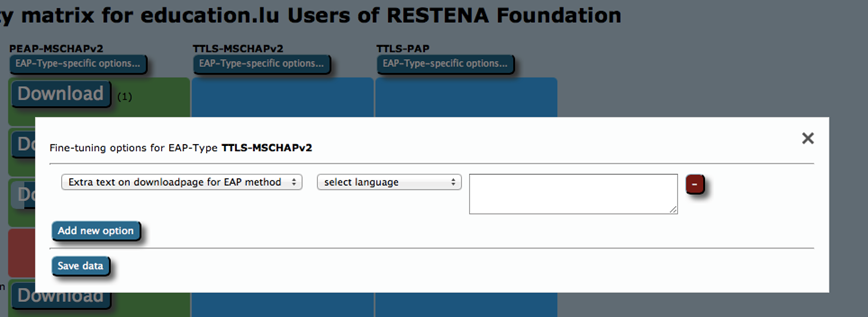
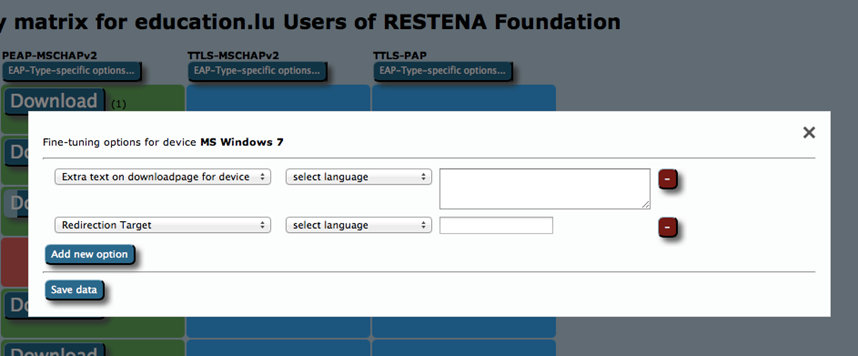
You can now click the download buttons and begin using the generated installers. This is also possible for redirected devices; although your users don’t get this installer from CAT, an admin might want to have it anyway to include in your own eduroam support pages.
Updating your CAT Profile to use the geteduroam app as the default choice for Android 8+
- Visit https://cat.eduroam.org and select Manage/eduroam® admin access
- Sign in using your preferred Identity Provider
- For the profile, select Installer-Fine Tuning and Download
Under Android 8 and higher
- Click Device-specific options…
- Select Show the dedicated geteduroam download page for this device from the dropdown menu and ensure the box is checked.
- Click Save Data
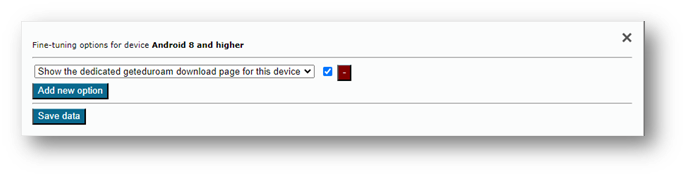
- Repeat for other profiles.
Android 8+ users visiting cat.eduroam.org for your institution will now see the following screen instead:
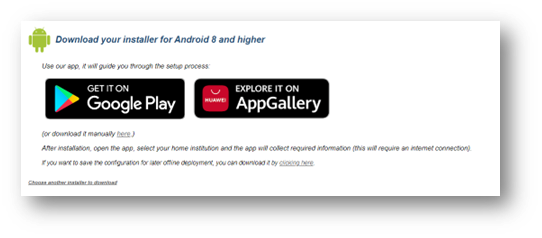
5. Installer visibility on the user download page
You are in full control of which installers, if any, you want to show as well as when you want to show them on the CAT end-user download pages.
Your control options are:
- Make the EAP profile visible but redirect users to your own support pages (entry is listed, but no download on the public page). This can be set in Profile options – see screenshot.
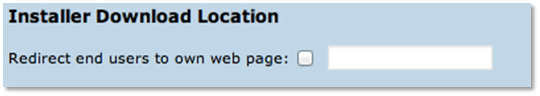
- Make the EAP profile visible with installers but redirect certain devices to your own pages. Use the Fine-Tuning matrix to set the Redirect option for the device (see previous section).
- Make all installers visible.
All three options require confirmation that you have entered all details and have reviewed the profile to be “production-ready”. Details of your EAP deployment will not be made visible until you have declared your data is set to production-ready. Do this by adding the option with that same name in your Profile properties.
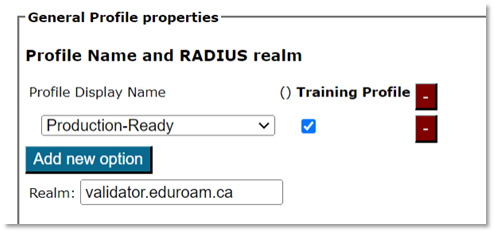
The visibility status of your EAP deployment is indicated with either a green (published) or yellow (unpublished) status icon on the Profile info (see screenshot). If the status is yellow, you can hover with your mouse over it to get a more detailed explanation why the profile is not published.
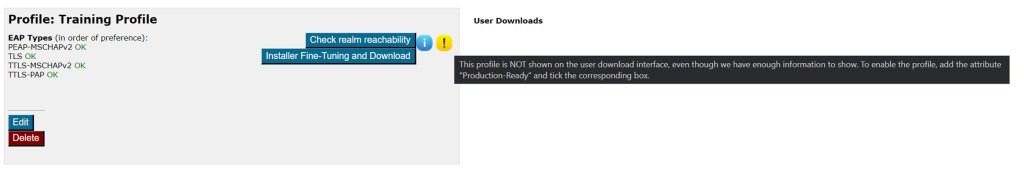
6. Verifying your RADIUS setup
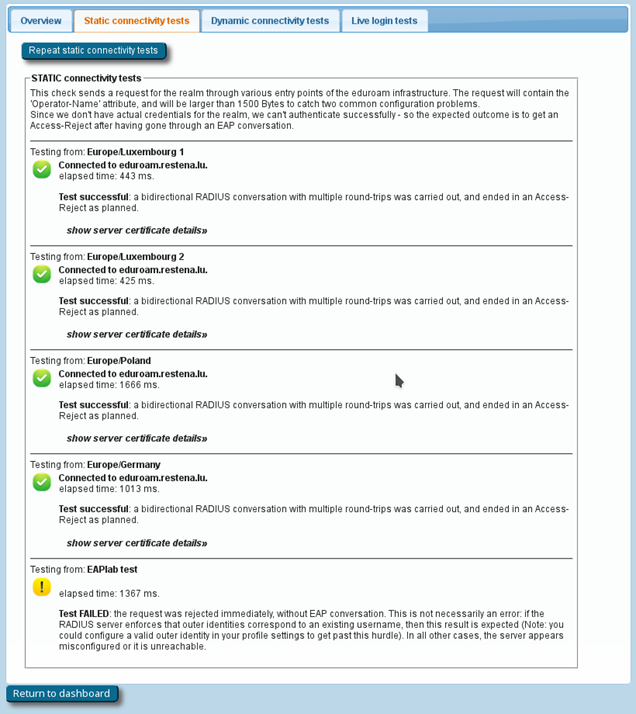
If you have supplied the CAT with the realm you are using in eduroam, an extra service is enabled: the CAT can send live data probes through the eduroam infrastructure to see if your realm’s RADIUS server is reachable and whether it passes various sanity checks. These tests are triggered by clicking Check realm reachability. You will see an overview page while various tests are run in the background:
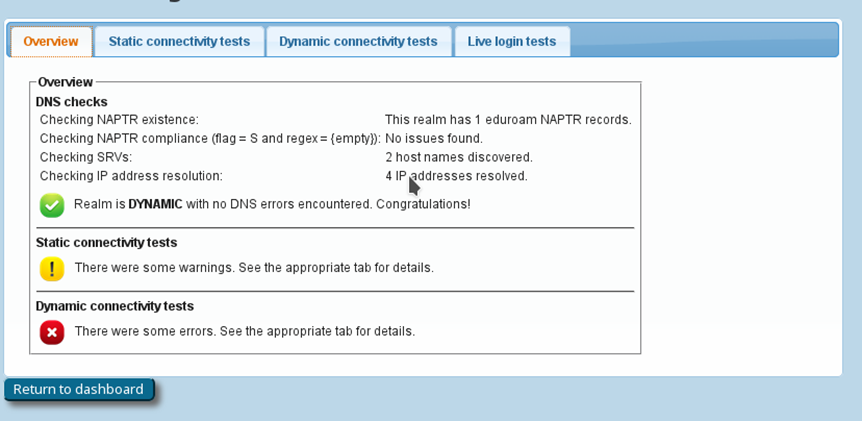
The tests will take a few moments and will give you an in-depth overview of how your RADIUS server is doing in the world of eduroam.
The tests include:
- A DNS check to determine whether your realm is publishing NAPTR records for eduroam Dynamic Discovery for RADIUS over TLS; and if so, whether all DNS records are correct (if you don’t know what Dynamic Discovery is, please talk to your national federation operator – it’s cool!). If the DNS checks were successful, the CAT will make actual use of the discovered RADIUS Dynamic Discovery server targets and try to connect. It will present a mix of valid and invalid certificates and will check whether the server acted correctly on receipt of these certificates.
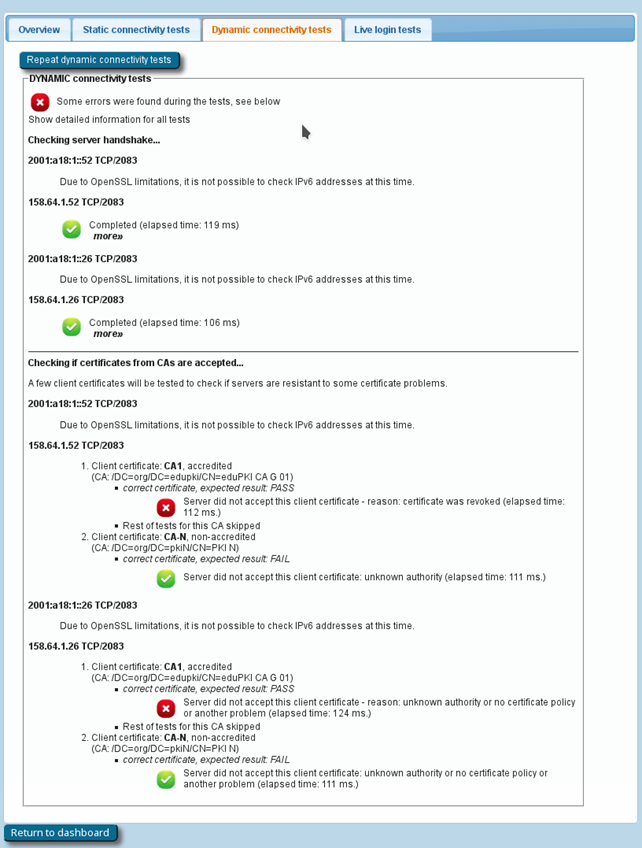
- The results of actual authentication tests, sent the moment you clicked “Check realm reachability: these will not log anybody in (we don’t have actual user credentials) but even with the planned failed authentication, the CAT tool can still run several diagnostics to ensure a good experience.
The results will flag any issues that require action, for example:
- Authentication round-trip times to your realm that take more than 5 seconds are considered suspicious.
- Your server must be able to send and receive UDP fragments (some firewalls incorrectly filter these).
- There are some RADIUS attributes that are commonly present in authentication requests; some servers behave strangely on receipt – CANARIE will reach out if yours has an issue.
- Checks regarding the structure and validity of your server, intermediate and root CA certificates. These checks are thorough, covering everything described on the EAP Server Considerations page.
Below is a typical output if your server certificate is “from the 1990s” (i.e., has not been updated with recent recommendations and requirements for server certificates).
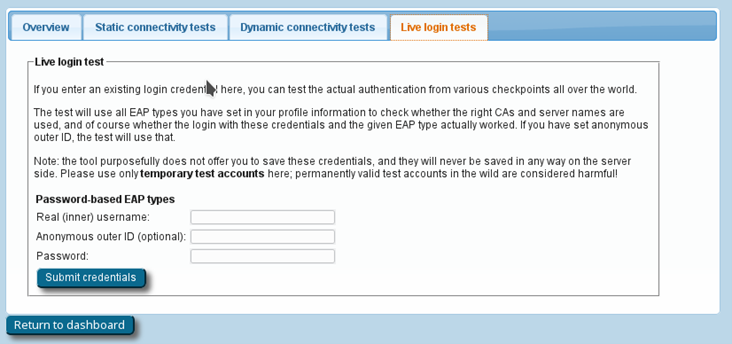
If you feel comfortable giving CAT access to short-lived, real authentication credentials (for debugging purposes with test user accounts only), you can run an actual positive authentication test, in which case we can run further diagnostics.
7. Other
7.1 User API
A full access web API makes it possible to create different user interfaces to CAT.
Specifically, you can:
- list countries with configured organizations,
- list organizations globally or within a country,
- list profiles within organization,
- ask for the organization logo or even geolocate users’ IP addresses, and
- download installers for given user profiles and devices.
For more detail, check out this tutorial from GEANT.
7.2 Silent Windows installers
Windows installers can be run silently with the -s flag, which is useful for organizations that want to build the installers into their own, larger ones.
8. Replacing the RADIUS server root CA certificate
When your RADIUS server’s root CA certificate is about to expire and you need to replace it with a new one, the new CA certificate needs to be communicated to all your users’ devices. The procedure for this is as follows:
- Create a new “migration” eduroam profile in eduroam CAT, containing both the current and new root CA certificates. All previous eduroam CAT profiles should be deleted to avoid them being used.
Note: This new profile will not work as intended for Android < 7.1 devices. - Require all new and existing end-users to download the new “migration” profile. Their devices (except for Android < 7.1), will then be capable of trusting both the current and the new CA, and will accept server certificates from either CA.
- Once you are confident that all end-user devices have the “migration” profile installed, apply the new server certificate on the Radius server(s). Ideally, the host name in the certificate CN/subjectAltNames should be identical to the old server certificate.
Note: Android < 7.1 devices configured with the old root CA will now no longer be able to authenticate. Users will need to install a new profile containing just the new root CA. - Create a new “permanent” eduroam profile in eduroam CAT, containing only the new root CA certificate. Delete the “migration” eduroam profile.
- Require all existing Android < 7.1 users, and all new users, to download the new profile.
9. Getting Help with eduroam CAT
Before reaching out for help, please follow the checklist below. It helps us better assist you when we know where you are in the process.
CAT Profile Checklist
Configuring an Organization
- Invitation received & signed in to https://cat.eduroam.org/
- Anonymous outer ID is set
- Certificate/CN is aligned to RADIUS server
- Appropriate EAP methods are set
- Installer testing & fine-tuning is complete
- CAT profile(s) are published
Communication & Adoption
- Communications and engagement campaign
- Measuring adoption
Infrastructure Enhancements
- eduroam-assist SSID to aid onboarding
- RADIUS servers reconfigured to mandate CAT for connectivity
If you have any questions about the eduroam CAT website or the underlying software, don’t hesitate to join the mailing list [email protected]. Tip: please subscribe to the list before posting – this guarantees that you’ll still get replies even if someone forgets a “reply to all”. It also ensures that your post won’t end up in the spam folder.


